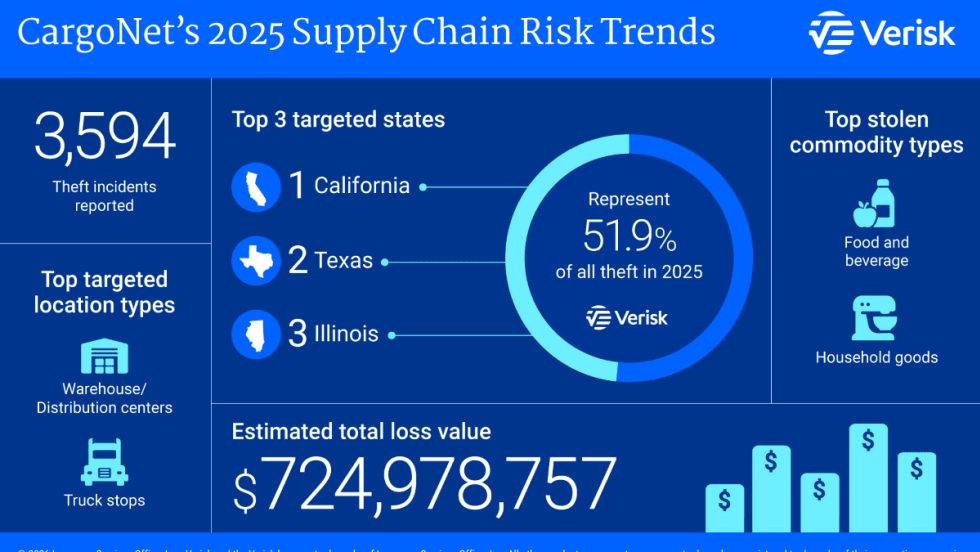
Cyber-enabled cargo theft shows why converged security is becoming essential for trucking fleets, linking cybersecurity, operations, and physical safeguards.
The cyberthreat landscape has changed, and that change is forcing trucking companies to rethink what “security” actually means.
Modern security incidents often don’t begin with a bang. They begin quietly — with a compromised login, a spoofed email, or a manipulated business process that looks legitimate on the surface.
By the time data is stolen or a trailer goes missing, it’s too late for prevention. All that is left is to minimize the damage.
This evolution has exposed a hard truth for the transportation industry: Cybersecurity, operational security, and physical security can no longer be treated as separate problems.
Cyber-enabled crime has become an increasingly common tactic in trucking operations, as attackers exploit digital access, routine workflows, and trust-based processes to gain control of physical freight.
In a highly connected freight ecosystem, they are tightly linked, and weaknesses in one area routinely cascade into the others. These three areas now must be considered interdependent parts of a single whole.
When Cargo Theft Became a Digital Crime
Traditional cargo theft was opportunistic. Criminals targeted unsecured locations, predictable routes, or isolated insider access.
Cyber-enabled cargo theft is far more deliberate and far more sophisticated, leveraging operational weaknesses, physical control gaps, and cybersecurity vulnerabilities with surgical precision.
Industry reporting has tied the rise in cargo theft to organized criminal networks, which study freight flows, dispatch processes, and verification gaps before exploiting them at scale.
Attackers routinely impersonate legitimate carriers or brokers, exploit dispatch and load-board processes, and manipulate trust relationships between trading partners. Organized criminals study how freight moves, how decisions are made, and where verification is weakest. Then they simply log in, follow normal workflows, and redirect freight under false pretenses.
That’s why many fleets are surprised when theft occurs. The systems didn’t fail in obvious ways. No alarm bells rang, and the processes worked — for the wrong people.
Why Siloed Defenses Keep Falling Short
Fleets have invested heavily in cybersecurity tools, yard security, and operational safety programs as separate initiatives. Each has value on its own, but cyber-enabled cargo theft thrives in the gaps between them:
A phishing email can trigger a fraudulent pickup.
A weak vendor onboarding process can enable a stolen load.
A delay in recognizing suspicious activity can turn a recoverable incident into a total loss.
None of these failures exists entirely in one domain. That’s why treating them separately no longer works.
Converged security takes a different approach.
It recognizes that cyber controls, operational processes, and physical safeguards all protect the same thing: the integrity of the organization and the shipments for which they are responsible. When cybersecurity, operational security, and physical security controls are designed as components of a holistic, converged security strategy, the bad actors are left with far fewer weak points to exploit.
Cargo Crime Is Really a Resilience Problem
Cargo theft is often discussed as a physical crime issue, but its root causes point to something much more complex.
The same weaknesses that enable cyber-enabled theft also increase exposure to ransomware, data theft, and extortion. That’s why some of the most effective cargo-theft mitigations don’t feel like traditional security at all. They look like good cyber hygiene and clearly defined business processes: Role-based access controls (RBAC), consistent verification, documented processes, and well-rehearsed response plans.
Fleets that invest in these areas aren’t just reducing their risk of cargo crime. They’re strengthening their resilience against disruptions of any kind, physical or digital.
Where Trucking Fleets Still Get Stuck in Shifting Their Cybersecurity Approach
Despite growing awareness, many organizations struggle to make this shift.
All too often, trust is still assumed instead of verified. Transportation is a fast-paced industry. Warning signs are regularly noticed but not escalated for fear of slowing things down and losing freight to a competitor.
Attackers understand this hesitation and exploit it. They depend on speed, routine, and the pressure to keep freight moving. The more informal and fragmented security becomes, the easier it is for them to blend in.
Cybersecurity is too often viewed as an IT responsibility rather than an operational one. This is one of the most dangerous assumptions in transportation security.
Traditional IT should support the infrastructure and ensure redundancies and disaster recovery capabilities.
Security, and more specifically cybersecurity, should be baked into the core of business processes across every single department in the organization in a deliberate and consistent manner, with skilled and accountable leadership at the helm.
What Converged Security at a Trucking Company Looks Like in Practice
Trucking fleets that are successfully reducing cargo crime and data theft tend to approach security as a shared responsibility. Cyber, operations, safety, and leadership work from the same playbook. Employees understand why verification matters and feel empowered to question anomalies. Reporting is encouraged early, not after the damage is done.
This doesn’t mean supporting “paralysis by analysis” or the overthinking of every single decision. It means designing processes that make the secure choice the easy choice, especially under pressure.
The current cyber-enabled cargo crime rates are not a temporary spike or a niche problem only affecting certain types of freight. It’s the natural outcome of an industry that runs on digital systems, shared platforms, and high-trust relationships while relying on a siloed approach to security.
The lines between physical crime and digital crime have dissolved. It is time to throw out the divisions between cybersecurity, operational security, and physical security.